Series: Setting up Oracle Cloud VM - II
This is a continuation from: [[001 Signing up for new Oracle Cloud Account]]
✅ Step 2: Setup Virtual Cloud Network (VCN)
🎯 Goal:
Create a custom VCN with:
- One public subnet (for your reverse proxy VM with Traefik)
- One or more private subnets (for internal VMs like Keycloak, Supabase, Redis, etc.)
- Allow internal communication and secure public access only where needed
🔹 2.1. Key Concepts (for certification + blog)
| Term | Explanation |
|---|---|
| VCN (Virtual Cloud Network) | Your private, isolated cloud network in OCI |
| Subnet | A logical division of a VCN (either public or private) |
| Internet Gateway (IG) | Allows outbound/inbound access to the internet |
| NAT Gateway | Lets private subnet instances access the internet (outbound only) |
| Security List / NSG | Acts like a firewall – controls traffic rules |
| Route Table | Determines how traffic is routed within or outside the VCN |
📘 DevOps Certification Tip: You're expected to know how to design and secure VCNs using subnets, gateways, and security lists.
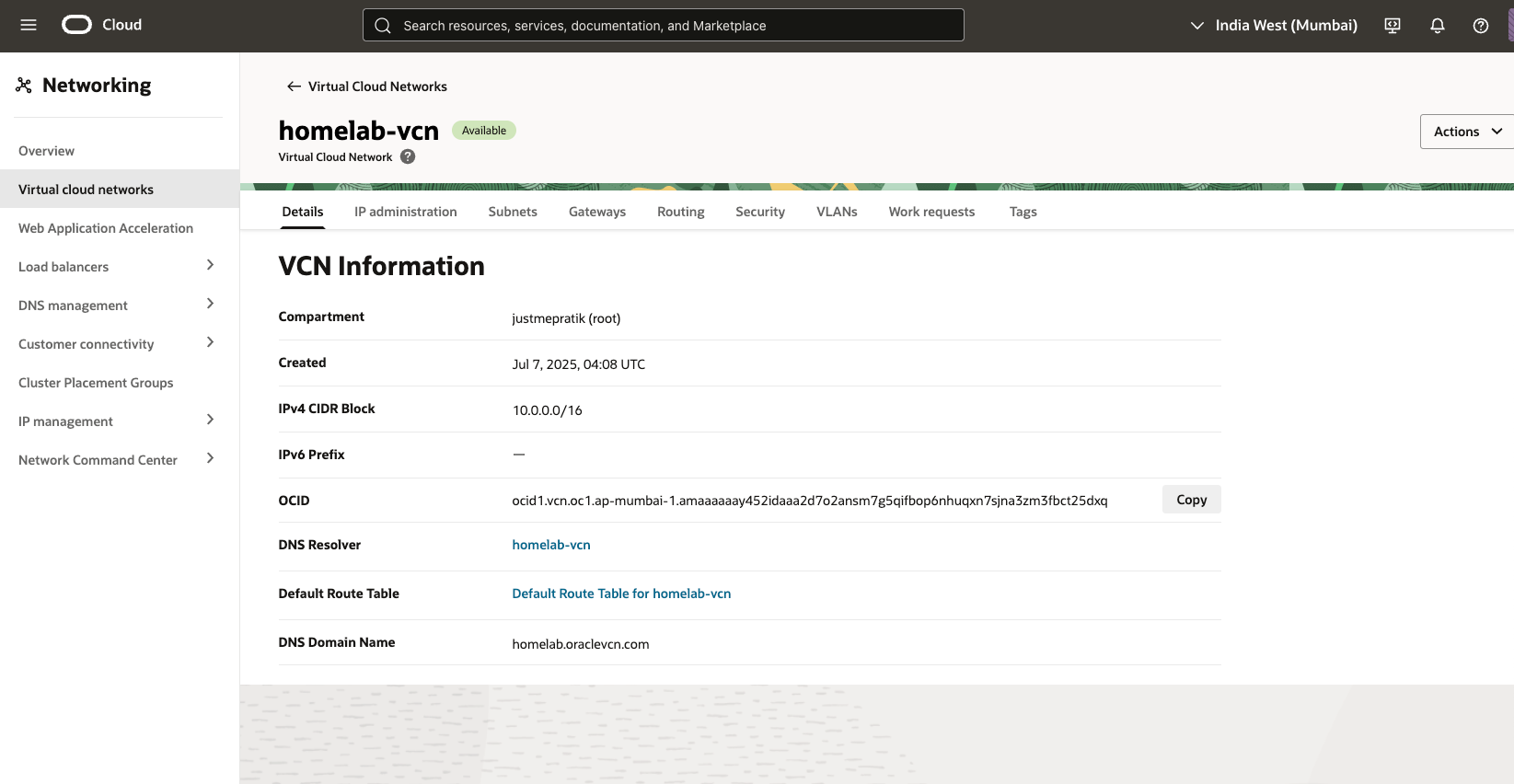
🛠️ 2.2. Create VCN (with subnets, route table, gateways)
- Go to: ☰ Networking → Virtual Cloud Networks
- Click Create VCN
- Choose "VCN with Internet Connectivity"
- Fill details:
| Field | Value |
|---|---|
| Name | homelab-vcn |
| CIDR block | 10.0.0.0/16 |
| DNS label | homelab (auto-filled) |
| Create Internet Gateway | ✅ Yes |
| Create NAT Gateway | ✅ Yes (for private subnet) |
| Enable DNS resolution | ✅ Yes |
| Create Service Gateway | ⬜ Skip (not needed for now) |
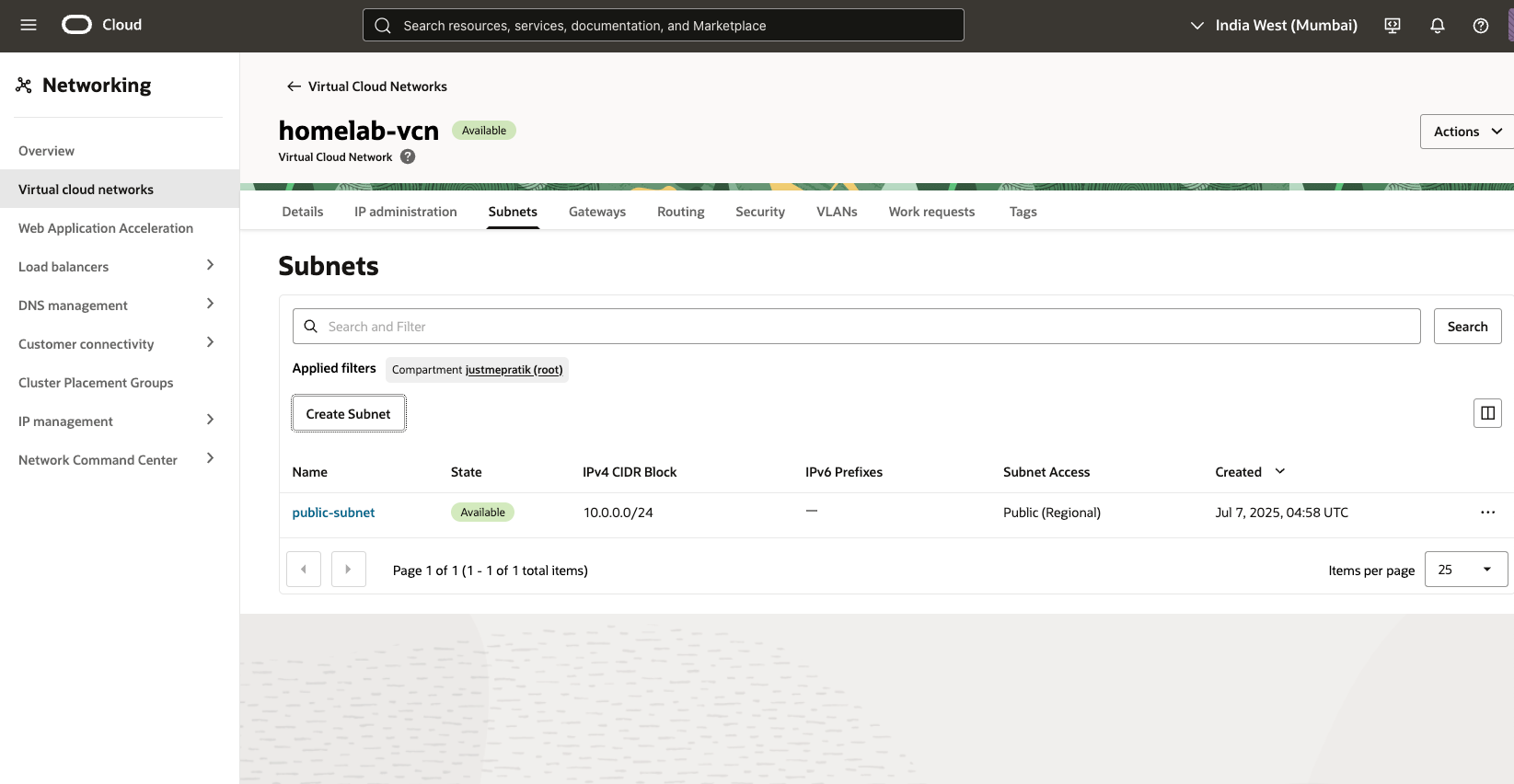
- Name:
public-subnet - CIDR:
10.0.0.0/24 - Subnet type: Regional
- Route Table: attach with Internet Gateway
- DHCP Options: default
- DNS Label:
public - Create a private subnet:
- Name:
private-subnet - CIDR:
10.0.1.0/24 - Subnet type: Regional
- Route Table: attach with NAT Gateway
- DNS Label:
private
- Name:
Create a public subnet:
🔐 2.3. Security Lists (Firewall rules)
For both public and private subnets:
- Allow intra-VCN traffic (default rule)
- Add custom ingress rules based on services (later, e.g., 8080 for Keycloak, 443 for Traefik)
Example: for public subnet
Source CIDR: 0.0.0.0/0
Protocol: TCP
Port Range: 80, 443
Description: Allow HTTP/HTTPS to Traefik
✅ What You Have After This
| Resource | Description |
|---|---|
homelab-vcn | Main VCN for project |
public-subnet | Hosts Traefik reverse proxy |
private-subnet | Hosts Keycloak, Postgres, Supabase, Redis |
| Internet Gateway | Public internet access |
| NAT Gateway | Allows private subnet to fetch updates |
| Security Lists | Basic firewall rules |
✅ Summary
| Task | Status |
|---|---|
Created custom VCN (homelab-vcn) | ✅ |
| Set up public and private subnets | ✅ |
| Configured route tables + gateways | ✅ |
| Allowed minimal, secure firewall rules | ✅ |
See you in next part: [[003 Creating Traefik VM Instance]]